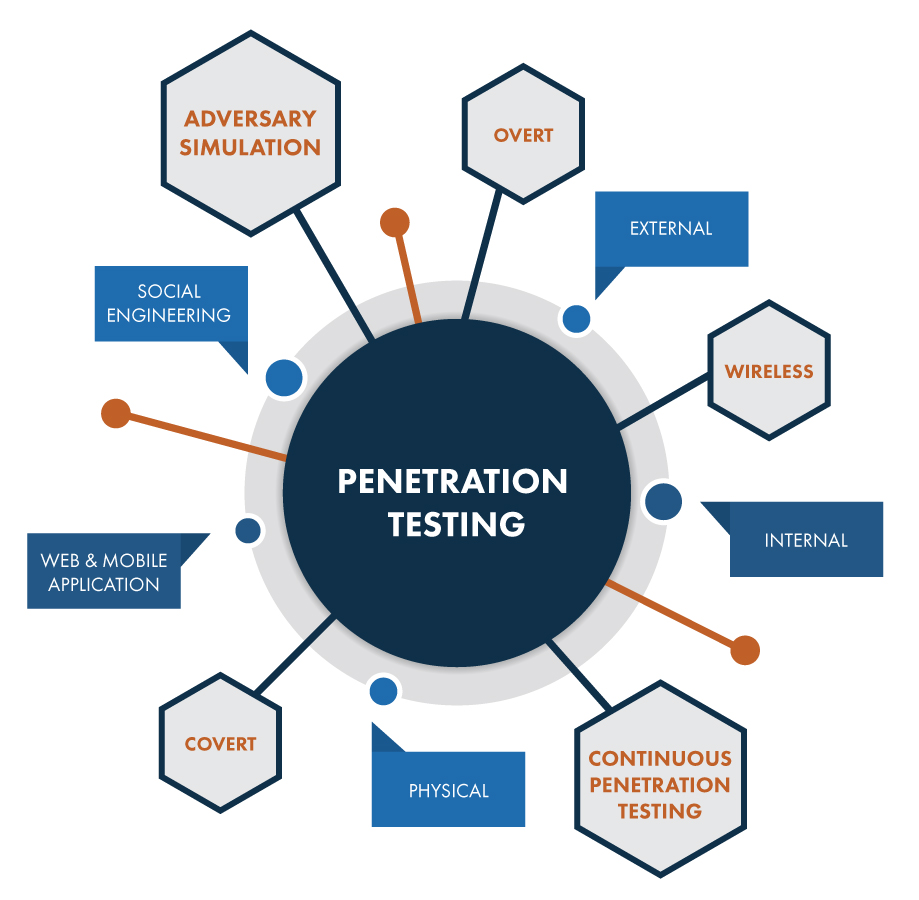
Is a method of testing, measuring and enhancing established security measures on information systems and support areas.
It may be conducted to complement background investigations and ensure social engineering and networking safety. Is implemented by simulating malicious attacks from an organization’s internal and external users. The entire system is then analyzed for potential vulnerabilities. A plan that communicates test objectives, timetables and resources is developed prior to actual pen-testing.
Pen-testing is an invaluable process for a number of reasons, including the following:
- Minimal security breach potential ensures system reliability.
- Complies with regulatory or other agencies.
- Demonstrates a good-faith effort to protect customer information
Pen-testing tools include:
- Commercial off-the-shelf (COTS) or prebuilt equipment and/or software applications
- Proprietary enterprise applications (EA)
- Potentially comprisable phone and wireless systems
- Physical controls
- Websites